Single Sign-on (Enterprise)
Single-Sign-On lets users sign-in once and then access multiple different resources protected by that same authentication service.
SSO (Single-Sign-On) is convenient for users since they don't need to remember, manage and enter multiple sets of credentials. SSO is often more secure because the security is centralized and better managed.
How Single Sign-On works
When SSO is enabled then dbFront won't show a login screen. If dbFront encounters a user that needs authentication it will redirect that user to the configured SSO provider. It is the SSO provider's responsibility to authenticate the user and then return them to dbFront.
dbFront implements SSO using the SAML 2 protocol. For more details see:
- https://en.wikipedia.org/wiki/SAML_2.0
- https://docs.microsoft.com/en-us/azure/active-directory/develop/single-sign-on-saml-protocol
Setting up Single Sign-on
Note: Single Sign-on Authentication is a global setting that overrides other authentication options. Unlike Active Directory / Windows Authentication or Database Authentication, Single Sign-on can't be limited to specific connections.
Setting up, editing or removing, SSO authentication requires special local server access. To set up SSO you should:
- Directly log-in on, or remote desktop to, the web server hosting dbFront,
- Once connected you can run dbFront in a browser with the URL http://localhost/dbFront. Note: The URL must start with http://localhost,
- Login to dbFront using an administrative account (local machine or domain),
- From the dbFront main menu click [Help] / [Settings],
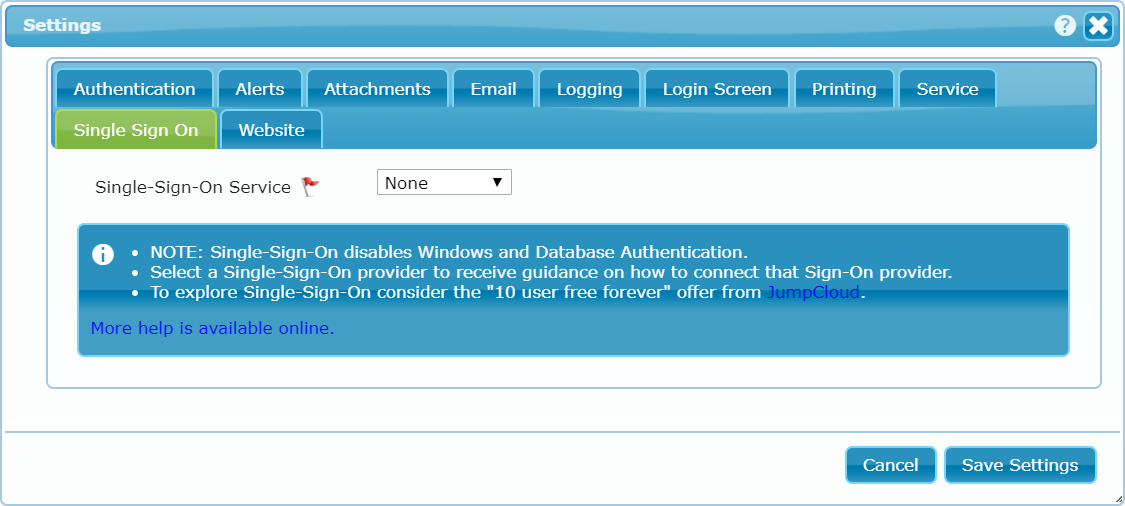
- From the Settings Dialog click on the "Single-Sign-On" tab.
On the SSO tab, you will be able to select the desired Sign-On provider. The options available for each vendor are generally the same but dbFront will use the vendor selection to provide customized help. The screen to the right is shown if no vendor is selected.
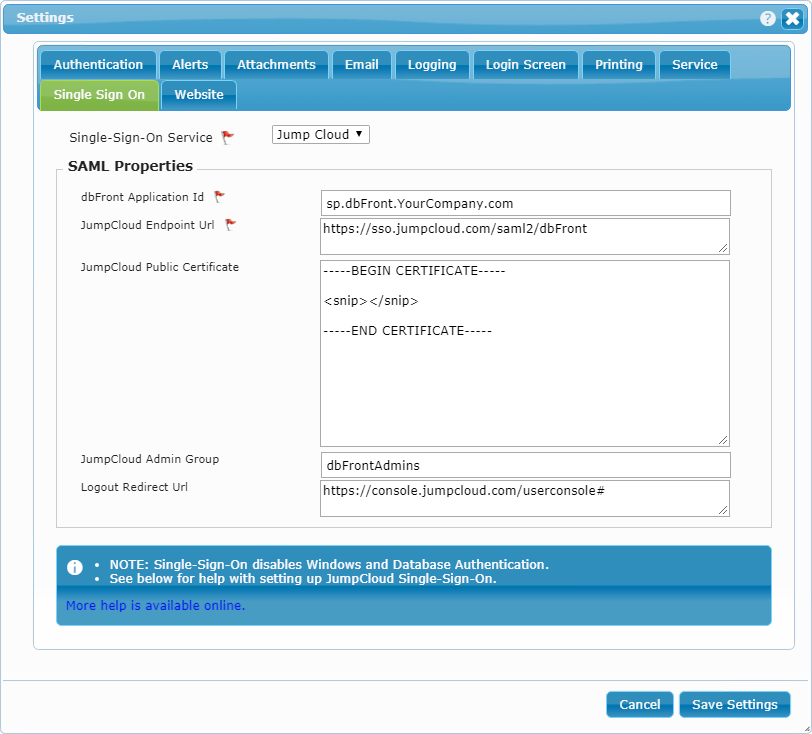
Once a vendor is selected, dbFront will show the configuration fields. The screen below shows the vendor JumpCloud with some suggested settings. Clicking on the help link will show the vendor-specific help.
- dbFront Application Id: Vendor unique and often vendor specified ID for your application.
- Vendor Endpoint URL: Vendor hosted and often application-specific URL to the authentication service for your application.
- Vendor Public Certificate: If specified, this vendor provided certificate is used to validate vendor authentication responses.
- Vendor Admin Group: The user group set up at the SSO intended for Admin users. All members of this group will be given Admin access to dbFront.
- Logout Redirect URL: dbFront will redirect users to this URL when they log-off from dbFront.
NOTE: dbFront purposely does not log-out from the entire SSO session. It only closes the dbFront session and redirects the user to the specified URL.
Testing Single-Sign-On with dbFront
dbFront will record debugging information if there is a login failure. You can enable extra logging from the setup screen. This can include the full SAML 2 messages. For more details see: Troubleshooting.
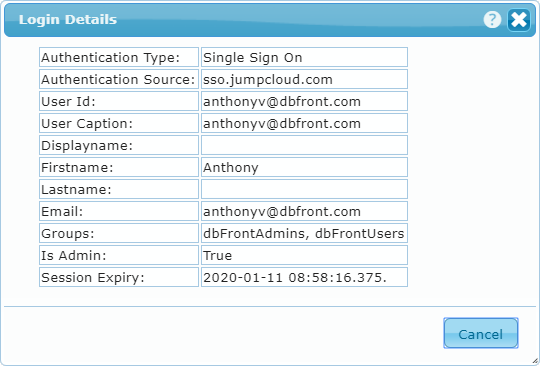
When a user is logged in they can see their login details from the user menu at the top right of the screen. This can be helpful when trying to determine why user access is incorrect. The screen to the right is an example of what you might see.
If you don't currently have an SSO vendor then we suggest signing up for a free JumpCloud account and following the JumpCloud specific setup instructions. For more details see:
- JumpCloud Free Forever account: JumpCloud Sign up
- dbFront to JumpCloud setup: JumpCloud Setup
Vendor-Specific Setup instructions
The following vendor-specific instructions are provided for your convenience. The SSO implementation in dbFront is SAML2 compliant so most vendors are supported even if specific instructions are not provided.
Trouble Shooting
For a list of Single-Sign-On issues and answers see: Single-Sign-On Questions
More Security Options
For more security options see: Authentication Overview