Penetration Testing
If your dbFront installation is going to be public, then we strongly recommend signing up for a free Probely account to validate that your dbFront configuration is secure. dbFront 1.4.2 and higher allow you to perform a quick security scan, but it is limited to catching common, easy-to-spot issues.
We perform penetration testing using the automated SAAS penetration tool Probely. Automated penetration testing is not as in-depth as manual penetration testing, but automated tests are great at catching server configuration issues and many other development and implementation mistakes.
NOTE: Before proceeding, you must enable SSL on your webserver.
Probely Setup
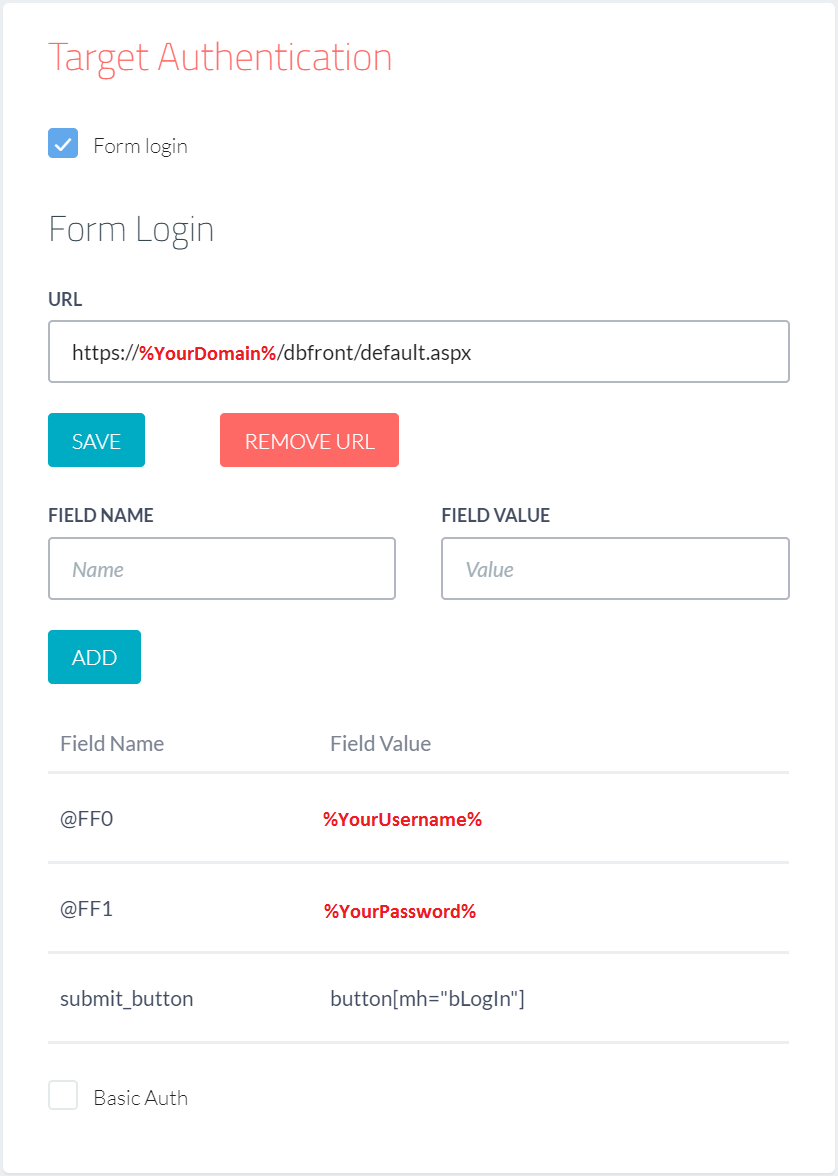
When preparing Probely to scan your dbFront install, you should enter the following details:
NOTE: Replace the values in RED with values appropriate to your environment.
- Address (URL): https://%YourDomain%/dbFront/default.aspx,
- Target Authentication: Select Form Login,
- Login URL: https://%YourDomain%/dbFront/default.aspx,
- Login Field Names:
- @FF0: %YourUsername%,
- @FF1: %YourPassword%,
- submit_button: button[mh="bLogIn"]
Once Probely is correctly configured, you can scan your site repeatedly and eliminate any security issues.
Secure Root Web.config
As part of securing your server, we recommend adding the following web.config contents to the root of your web server. These web.config additions will address several issues that the penetration scan is likely to find if not already addressed. You may need to adjust some settings to meet your environment and application requirements.
<system.webServer>
<httpProtocol>
<customHeaders>
<!-- Block Click Jacking -->
<remove name="X-Frame-Options"/>
<add name="X-Frame-Options" value="SAMEORIGIN" />
<!-- Enforce HSTS header -->
<remove name="Strict-Transport-Security"/>
<add name="Strict-Transport-Security" value="max-age=31536000;includeSubdomains"/>
<!-- Prevent Browser content sniffing -->
<remove name="X-Content-Type-Options"/>
<add name="X-Content-Type-Options" value="nosniff"/>
<!-- Prevent the leaking of URL params via Referrer -->
<remove name="Referrer-Policy"/>
<add name="Referrer-Policy" value="same-origin" />
<!-- Application Dependent Content-Security-Policy -->
<remove name="Content-Security-Policy"/>
<add name="Content-Security-Policy" value="
default-src 'self' 'unsafe-inline' 'unsafe-eval';
img-src 'self' data:;
frame-src 'self' https://dbFront.com;
frame-ancestors 'self';" />
</customHeaders>
</httpProtocol>
</system.webServer>
</configuration>
Common Issues
The suggested web.config changes in the preceding section should have dealt with a good portion of the issues raised by the security scan. Some further issues are covered below.
NOTE: As of dbFront 1.0.15.0470, we have dealt with all known application issues.
Secure Cookie Flag Required
If dbFront is installed on an SSL secured web server then you should add the following to the dbFront web.config file. The default path is [c:inetpubdbFrontweb.config].
<httpCookies requireSSL="true" />
</system.web>
NOTE: Adding requireSSL may block logins using IE. See: Session Key Failure
Weak cipher suites enabled / Outdated TLS protocol version 1.0 supported
Both preceding errors refer to the fact that older insecure protocols are enabled on your web server.
If your web server is directly exposed to the internet, you will need to remove/disable these protocols. A very helpful tool for managing the installed Cipher Suites is IISCrypto from Nartac Software.
- IISCrypto - Download
- Within IISCrypto, you can select the appropriate template, Best Practices or PCI 4.0 and apply that to your server.
NOTE: The Best Practices template will likely leave some older, less secure protocols enabled to allow your web server to support older browsers. Otherwise, older browsers will simply fail to connect.
If Cloudflare protects your web server, you will need to make a Cloudflare configuration change.
- Set the Minimum TLS Version to 1.1.
- The Minimum TLS Version setting is found in the menu [SSL/TLS] and submenu [Edge Certificates].
NOTE: Cloudflare automatically uses patched versions of older protocols to maximize your client reach. Therefore, this change may not actually improve server security. It just cleans up the Penetration Report. See the following for more detail: Cloudflare fixes for known issues.